A military commander wants to allocate his resources of airplanes
to targets over the next two days. At present the planes are located
at several bases. In particular, there are 10 bases and the number
of planes currently at base i is 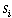 .
.
There are 12 targets. Six of the targets, numbered 1 through
6, are identified for day 1. The rest of the targets, numbered
7 through 12, are identified for day 2. Analysts have estimated
a dollar value of the damage caused by each plane that is sent
to a target. For target j, that damage value is 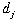 for the first five planes sent. For each additional plane up
to 10 planes the damage is 0.75
for the first five planes sent. For each additional plane up
to 10 planes the damage is 0.75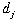 .
There is no value to sending more than 10. Of the planes sent
to a target j, a certain proportion will be lost due
to the target defenses. That proportion is .
There is no value to sending more than 10. Of the planes sent
to a target j, a certain proportion will be lost due
to the target defenses. That proportion is 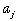 . .
A plane will leave its current base in the morning of day 1,
attack the target assigned to it. If it is not lost it will
land at one of the 10 bases and spend the night. On the next
day, it will leave the overnight base and attack the target
assigned for day 2. At the end of day 2, remaining planes will
return to one of the bases. Each base can accommodate no more
than 20 planes overnight. Part of the problem concerns travel
cost. The cost for a plane to travel between base i and
target j is 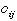 . .
One additional parameter that the commander must consider is
the cost of lost planes (and pilots). The cost of a lost plane
is k.
a. Set up the network model that will determine how many planes
to be sent from each base to each target in the two day time
horizon. The goal is to maximize the damage to the targets minus
the cost of travel and the cost of lost planes lost. Show the
conceptual model. You may neglect the integrality of the number
of planes.
b. How would you change the model to determine which targets
should be attacked in each the two days? A target may be assigned
to either day. A target can only be attacked once. (You may
have to use integer variables and side constraints.)
|



